Generate Remote Access Key Cpanel
The common way to connect to the server via SSH is to use a username and a password. But to increase security, you can use a pair of keys(a private one and a public one) to connect to the server.
1) To find and regenerate your server's Remote Access Key, scroll down in the menu to Cluster/Remote Access. 2) Click Setup Remote Access Key. Here is your current access key, in the greyed-out textarea at right. 3) Press this button to Generate a New Key. In the top right corner of the page, click Add deploy key. A new page will appear. In the Title text box, enter a display name for the key. In the Key text box, paste the entire SSH key. If you want to push code from your cPanel account to your GitHub account, select the Allow write access checkbox.
The public key will be on the server. The private key will be on your computer. When you are trying to connect, the server compares the two keys. If they are the right ones, you will be able to access it.
We will show in this post how to generate the pair of keys and connect to your server with PuTTY.
To generate and use public and private keys in cPanel:
1.Log in to cPanel
2.Scroll down to the SECURITY section -> SSH Access
Generate Remote Access Key Cpanel Server
3.Click the Manage SSH Keys button
4.Click the +Generate a New Key button
5.You are now on a page with a title Generating a Public Key. Here, choose:
-Key Name – you can leave the default value
-Key Password – enter the password for the key and confirm it
-Key Type (RSA or DSA) – let the default value
-Key Size (2048 or 4096) – let the default value
cPanel mentions:
RSA vs DSA: RSA and DSA are encryption algorithms used to encrypt your key. DSA is faster for Key Generation and Signing and RSA is faster for Verification.
6.Click the Generate Key button. You will see a confirmation message: Key Generation Complete! with some details:
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/username/.ssh/id_rsa.
Your public key has been saved in /home/username/.ssh/id_rsa.pub.
The key fingerprint is:
b7:9a:55:59:c1:a7:6a:31:5c:9a:40:50:e9:73:24:a0
7.Click the Go Back link
8.Now you need to authorize the public key. (the Authorization Status is not authorized). Click the Manage link.
9.You will see a message The key with the name “id_rsa” is currently “not authorized” for use when connecting to this account. Click the Authorize button. The success message is: The key “id_rsa.pub” has been authorized.
10.Click the Go Back link
11.Go to the Private Keys sections and click the View/Download link.
12.Here we will Convert the “id_rsa” key to PPK format. Enter the passphrase and click the Convert button.
13.You will see the key to be used in PuTTY. Click the Download key button and save the file to your computer (the filename is id_rsa.ppk)
14.Now start PuTTY on your computer and go to Connection->SSH->Auth. Here, browse and select the file you saved at 13. (Private key file for authentication)
Cpanel Webmail Access
15. Click the Open button. PuTTY will connect to the server. Enter the Passphrase when asked.
16.You are now connected to the server 🙂
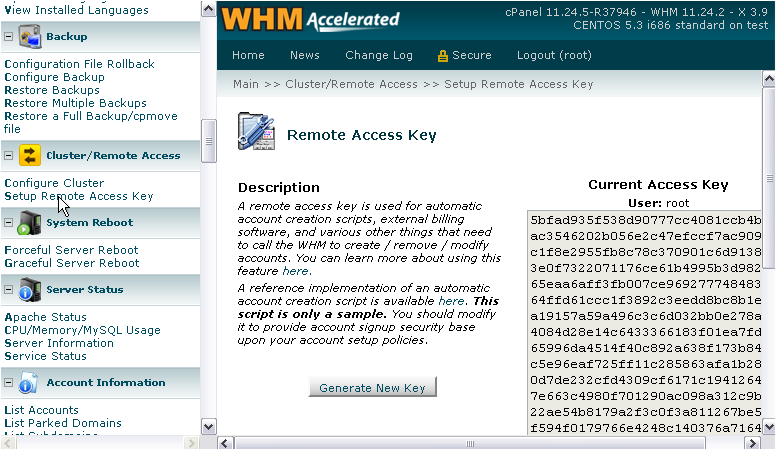
(Home >> Clusters >> Remote Access Key)
Overview
Gpg4win 8192 bit key generation. You can use this feature to generate an access key, which is also known as an access hash. You can use this access key for automatic account creation scripts, external billing software, and to allow servers in your DNS or configuration clusters to exchange records.
Generate a new access key
To generate a new access key, perform the following steps:
- Click Generate New Key.
- Copy and paste the new access key to the appropriate file on the remote server(s) that need to communicate with your web server.
- To configure a DNS server cluster, read our DNS Cluster documentation.
- To configure a configuration cluster, read our Configuration Cluster documentation.
Note
You can view the access hash via the command line in the /root/.accesshash file.
Access Key Signature
The Access Key Signature includes the first 32 characters of the remote access key, separated by colons (:).
You can use this signature to quickly check whether you have used the correct access key in interfaces that display the key in a shortened format.