Using An Image To Generate An Encryption Key
- Using An Image To Generate An Encryption Key Download
- Using An Image To Generate An Encryption Key Mean
- Using An Image To Generate An Encryption Key In Iphone
- Using An Image To Generate An Encryption Keyboard
- Using An Image To Generate An Encryption Key In Excel
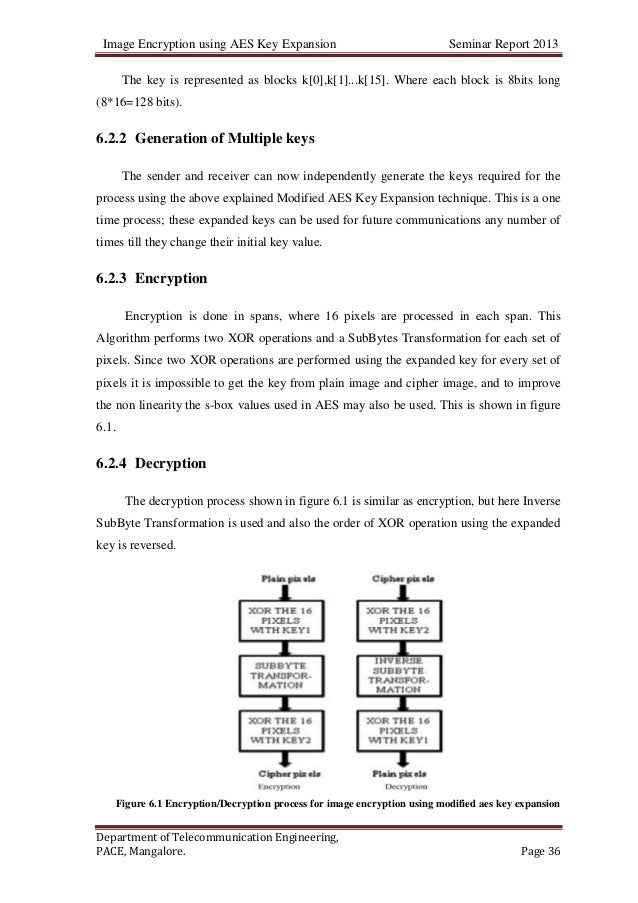
Azure managed disks automatically encrypt your data by default when persisting it to the cloud. Server-side encryption protects your data and helps you meet your organizational security and compliance commitments. Data in Azure managed disks is encrypted transparently using 256-bit AES encryption, one of the strongest block ciphers available, and is FIPS 140-2 compliant.
Encryption does not impact the performance of managed disks. There is no additional cost for the encryption.
May 28, 2015 This blog describes how to generate a private/public key pair using GPG version 1.4.5. The resulting public key will contain two keys, one key for signing and a subkey for encryption. This key can be used with HCM Fusion SaaS to encrypt/decrypt files as they are transferred to and from the UCM server. User input is noted in RED text. Feb 19, 2020 Scientists Crack Longest Encryption Key Ever. Image-segmentation algorithms looked at the pixels corresponding to the crystals. 'Using chemistry to generate random numbers may enhance the. Apr 03, 2018 You don’t need third-party utilities like VeraCrypt to create a secure, encrypted container for your sensitive files on your Mac. You can create an encrypted disk image using the built-in Disk Utility. To be fair, you can also create an encrypted container using the built-in BitLocker feature on Windows, but that requires you have a Professional or Enterprise edition.
For more information about the cryptographic modules underlying Azure managed disks, see Cryptography API: Next Generation
About encryption key management
You can rely on platform-managed keys for the encryption of your managed disk, or you can manage encryption using your own keys. If you choose to manage encryption with your own keys, you can specify a customer-managed key to use for encrypting and decrypting all data in managed disks.
The following sections describe each of the options for key management in greater detail.
Platform-managed keys
By default, managed disks use platform-managed encryption keys. As of June 10, 2017, all new managed disks, snapshots, images, and new data written to existing managed disks are automatically encrypted-at-rest with platform-managed keys.
Customer-managed keys
You can choose to manage encryption at the level of each managed disk, with your own keys. Server-side encryption for managed disks with customer-managed keys offers an integrated experience with Azure Key Vault. You can either import your RSA keys to your Key Vault or generate new RSA keys in Azure Key Vault.
Azure managed disks handles the encryption and decryption in a fully transparent fashion using envelope encryption. It encrypts data using an AES 256 based data encryption key (DEK), which is, in turn, protected using your keys. The Storage service generates data encryption keys and encrypts them with customer-managed keys using RSA encryption. The envelope encryption allows you to rotate (change) your keys periodically as per your compliance policies without impacting your VMs. When you rotate your keys, the Storage service re-encrypts the data encryption keys with the new customer-managed keys.
You have to grant access to managed disks in your Key Vault to use your keys for encrypting and decrypting the DEK. This allows you full control of your data and keys. You can disable your keys or revoke access to managed disks at any time. You can also audit the encryption key usage with Azure Key Vault monitoring to ensure that only managed disks or other trusted Azure services are accessing your keys.
For premium SSDs, standard SSDs, and standard HDDs: When you disable or delete your key, any VMs with disks using that key will automatically shut down. After this, the VMs will not be usable unless the key is enabled again or you assign a new key.
For ultra disks, when you disable or delete a key, any VMs with ultra disks using the key won't automatically shut down. Once you deallocate and restart the VMs then the disks will stop using the key and then VMs won't come back online. To bring the VMs back online, you must assign a new key or enable the existing key.
Download downloader manager for mac. The following diagram shows how managed disks use Azure Active Directory and Azure Key Vault to make requests using the customer-managed key:
The following list explains the diagram in more detail:
- An Azure Key Vault administrator creates key vault resources.
- The key vault admin either imports their RSA keys to Key Vault or generate new RSA keys in Key Vault.
- That administrator creates an instance of Disk Encryption Set resource, specifying an Azure Key Vault ID and a key URL. Disk Encryption Set is a new resource introduced for simplifying the key management for managed disks.
- When a disk encryption set is created, a system-assigned managed identity is created in Azure Active Directory (AD) and associated with the disk encryption set.
- The Azure key vault administrator then grants the managed identity permission to perform operations in the key vault.
- A VM user creates disks by associating them with the disk encryption set. The VM user can also enable server-side encryption with customer-managed keys for existing resources by associating them with the disk encryption set.
- Managed disks use the managed identity to send requests to the Azure Key Vault.
- For reading or writing data, managed disks sends requests to Azure Key Vault to encrypt (wrap) and decrypt (unwrap) the data encryption key in order to perform encryption and decryption of the data.
To revoke access to customer-managed keys, see Azure Key Vault PowerShell and Azure Key Vault CLI. Revoking access effectively blocks access to all data in the storage account, as the encryption key is inaccessible by Azure Storage.
Supported regions
For premium SSDs, standard SSDs, and standard HDDs, only the following regions currently support customer-managed keys:
- Available as a GA offering in the public regions and Azure Government regions.
For ultra disks, only the following regions support customer-managed keys as a GA offering:
- East US
- West US 2
Restrictions
For now, customer-managed keys have the following restrictions:
- If this feature is enabled for your disk, you cannot disable it.If you need to work around this, you must copy all the data to an entirely different managed disk that isn't using customer-managed keys.
- Only 'soft' and 'hard' RSA keys of size 2080 are supported, no other keys or sizes.
- Disks created from custom images that are encrypted using server-side encryption and customer-managed keys must be encrypted using the same customer-managed keys and must be in the same subscription.
- Snapshots created from disks that are encrypted with server-side encryption and customer-managed keys must be encrypted with the same customer-managed keys.
- Custom images encrypted using server-side encryption and customer-managed keys cannot be used in the shared image gallery.
- All resources related to your customer-managed keys (Azure Key Vaults, disk encryption sets, VMs, disks, and snapshots) must be in the same subscription and region.
- Disks, snapshots, and images encrypted with customer-managed keys cannot move to another subscription.
- If you use the Azure portal to create your disk encryption set, you cannot use snapshots for now.
- Managed disks encrypted using customer-managed keys cannot also be encrypted with Azure Disk Encryption.
PowerShell
Setting up your Azure Key Vault and DiskEncryptionSet
Make sure that you have installed latest Azure PowerShell version, and you are signed in to an Azure account in with Connect-AzAccount
Create an instance of Azure Key Vault and encryption key.
When creating the Key Vault instance, you must enable soft delete and purge protection. Soft delete ensures that the Key Vault holds a deleted key for a given retention period (90 day default). Purge protection ensures that a deleted key cannot be permanently deleted until the retention period lapses. These settings protect you from losing data due to accidental deletion. These settings are mandatory when using a Key Vault for encrypting managed disks.
Important
Do not camel case the region, if you do so you may experience problems when assigning additional disks to the resource in the Azure portal.
Create an instance of a DiskEncryptionSet.
Grant the DiskEncryptionSet resource access to the key vault.
Note
It may take few minutes for Azure to create the identity of your DiskEncryptionSet in your Azure Active Directory. If you get an error like 'Cannot find the Active Directory object' when running the following command, wait a few minutes and try again.
Create a VM using a Marketplace image, encrypting the OS and data disks with customer-managed keys
Create an empty disk encrypted using server-side encryption with customer-managed keys and attach it to a VM
Encrypt existing unattached managed disks
Your existing disks must not be attached to a running VM in order for you to encrypt them using the following script:
Create a virtual machine scale set using a Marketplace image, encrypting the OS and data disks with customer-managed keys
Change the key of a DiskEncryptionSet to rotate the key for all the resources referencing the DiskEncryptionSet
Find the status of server-side encryption of a disk
Important
Customer-managed keys rely on managed identities for Azure resources, a feature of Azure Active Directory (Azure AD). When you configure customer-managed keys, a managed identity is automatically assigned to your resources under the covers. If you subsequently move the subscription, resource group, or managed disk from one Azure AD directory to another, the managed identity associated with managed disks is not transferred to the new tenant, so customer-managed keys may no longer work. For more information, see Transferring a subscription between Azure AD directories.
Portal
Setting up customer-managed keys for your disks will require you to create resources in a particular order, if you're doing it for the first time. First, you will need to create and set up an Azure Key Vault.
Setting up your Azure Key Vault
Sign into the Azure portal.
Search for and select Key Vaults.
Important
Your Azure key vault, disk encryption set, VM, disks, and snapshots must all be in the same region and subscription for deployment to succeed.
Select +Add to create a new Key Vault.
Create a new resource group.
Enter a key vault name, select a region, and select a pricing tier.
Select Review + Create, verify your choices, then select Create.
Once your key vault finishes deploying, select it.
Select Keys under Settings.
Select Generate/Import.
Leave both Key Type set to RSA and RSA Key Size set to 2048.
Fill in the remaining selections as you like and then select Create.
Setting up your disk encryption set
Using An Image To Generate An Encryption Key Download
Search for Disk Encryption Sets and select it.
On the Disk Encryption Sets blade select +Add.
Select your resource group, name your encryption set, and select the same region as your key vault.
Select Key vault and key.
Select the key vault and key you created previously, as well as the version.
Press Select.
Select Review + Create and then Create.
Open the disk encryption set once it finishes creating and select the alert that pops up.
Two notifications should pop up and succeed. Doing this will allow you to use the disk encryption set with your key vault.
Deploy a VM
Now that you've created and set up your key vault and the disk encryption set, you can deploy a VM using the encryption.The VM deployment process is similar to the standard deployment process, the only differences are that you need to deploy the VM in the same region as your other resources and you opt to use a customer managed key.
Search for Virtual Machines and select + Add to create a VM.
On the Basic tab, select the same region as your disk encryption set and Azure Key Vault.
Fill in the other values on the Basic tab as you like.
On the Disks tab, select Encryption at rest with a customer-managed key.
Select your disk encryption set in the Disk encryption set drop-down.
Make the remaining selections as you like.
Enable on an existing disk
Caution
Enabling disk encryption on any disks attached to a VM will require that you stop the VM.
Navigate to a VM that is in the same region as one of your disk encryption sets.
Open the VM and select Stop.
After the VM has finished stopping, select Disks and then select the disk you want to encrypt.
Select Encryption and select Encryption at rest with a customer-managed key and then select your disk encryption set in the drop-down list.
Select Save.
Repeat this process for any other disks attached to the VM you'd like to encrypt.
When your disks finish switching over to customer-managed keys, if there are no there no other attached disks you'd like to encrypt, you may start your VM.
Important
Customer-managed keys rely on managed identities for Azure resources, a feature of Azure Active Directory (Azure AD). When you configure customer-managed keys, a managed identity is automatically assigned to your resources under the covers. If you subsequently move the subscription, resource group, or managed disk from one Azure AD directory to another, the managed identity associated with managed disks is not transferred to the new tenant, so customer-managed keys may no longer work. For more information, see Transferring a subscription between Azure AD directories.
Using An Image To Generate An Encryption Key Mean
Server-side encryption versus Azure disk encryption
Azure Disk Encryption leverages the BitLocker feature of Windows and the DM-Crypt feature of Linux to encrypt managed disks with customer-managed keys within the guest VM. Server-side encryption with customer-managed keys improves on ADE by enabling you to use any OS types and images for your VMs by encrypting data in the Storage service.
Next steps
-->Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data. The IV does not have to be secret, but should be changed for each session. Asymmetric algorithms require the creation of a public key and a private key. The public key can be made public to anyone, while the private key must known only by the party who will decrypt the data encrypted with the public key. This section describes how to generate and manage keys for both symmetric and asymmetric algorithms.
Symmetric Keys
The symmetric encryption classes supplied by the .NET Framework require a key and a new initialization vector (IV) to encrypt and decrypt data. Whenever you create a new instance of one of the managed symmetric cryptographic classes using the parameterless constructor, a new key and IV are automatically created. Anyone that you allow to decrypt your data must possess the same key and IV and use the same algorithm. Generally, a new key and IV should be created for every session, and neither the key nor IV should be stored for use in a later session.
To communicate a symmetric key and IV to a remote party, you would usually encrypt the symmetric key by using asymmetric encryption. Sending the key across an insecure network without encrypting it is unsafe, because anyone who intercepts the key and IV can then decrypt your data. For more information about exchanging data by using encryption, see Creating a Cryptographic Scheme.
The following example shows the creation of a new instance of the TripleDESCryptoServiceProvider class that implements the TripleDES algorithm.
When the previous code is executed, a new key and IV are generated and placed in the Key and IV properties, respectively.
Sometimes you might need to generate multiple keys. In this situation, you can create a new instance of a class that implements a symmetric algorithm and then create a new key and IV by calling the GenerateKey and GenerateIV methods. The following code example illustrates how to create new keys and IVs after a new instance of the symmetric cryptographic class has been made.
When the previous code is executed, a key and IV are generated when the new instance of TripleDESCryptoServiceProvider is made. Another key and IV are created when the GenerateKey and GenerateIV methods are called.
Asymmetric Keys
The .NET Framework provides the RSACryptoServiceProvider and DSACryptoServiceProvider classes for asymmetric encryption. These classes create a public/private key pair when you use the parameterless constructor to create a new instance. Asymmetric keys can be either stored for use in multiple sessions or generated for one session only. While the public key can be made generally available, the private key should be closely guarded.
A public/private key pair is generated whenever a new instance of an asymmetric algorithm class is created. After a new instance of the class is created, the key information can be extracted using one of two methods:
The ToXmlString method, which returns an XML representation of the key information.
The ExportParameters method, which returns an RSAParameters structure that holds the key information.
Both methods accept a Boolean value that indicates whether to return only the public key information or to return both the public-key and the private-key information. An RSACryptoServiceProvider class can be initialized to the value of an RSAParameters structure by using the ImportParameters method.
Using An Image To Generate An Encryption Key In Iphone
Asymmetric private keys should never be stored verbatim or in plain text on the local computer. If you need to store a private key, you should use a key container. For more on how to store a private key in a key container, see How to: Store Asymmetric Keys in a Key Container.
Using An Image To Generate An Encryption Keyboard
The following code example creates a new instance of the RSACryptoServiceProvider class, creating a public/private key pair, and saves the public key information to an RSAParameters structure.